Warren Buffer writeup- Forensics – Hack The Box University CTF 2020 (HTB UNI CTF 2020)

This file is given:
The challenge gives us a pcap file, so lets analyze it using Wireshark!
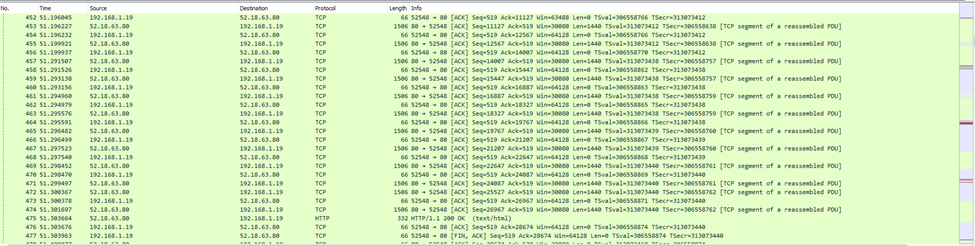
Searching Protocols we find some HTTP requests.
Lets apply a display filter for HTTP requests only!
We discover that 2 bytes of every User-Agent header can be different for each request.
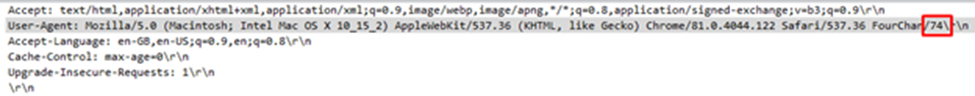
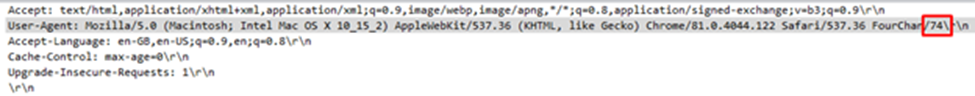
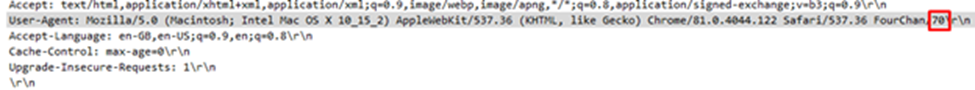
It could be hex! Lets strip those 2 bytes from User-Agent header of every request and assemble them!
We can write a python script to parse those bytes from every request or we can just use tshark and extract only those 2 bytes from each request.
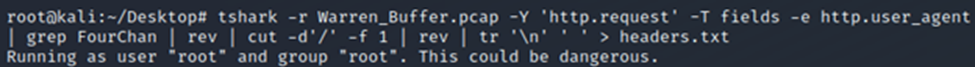
We convert from hex.
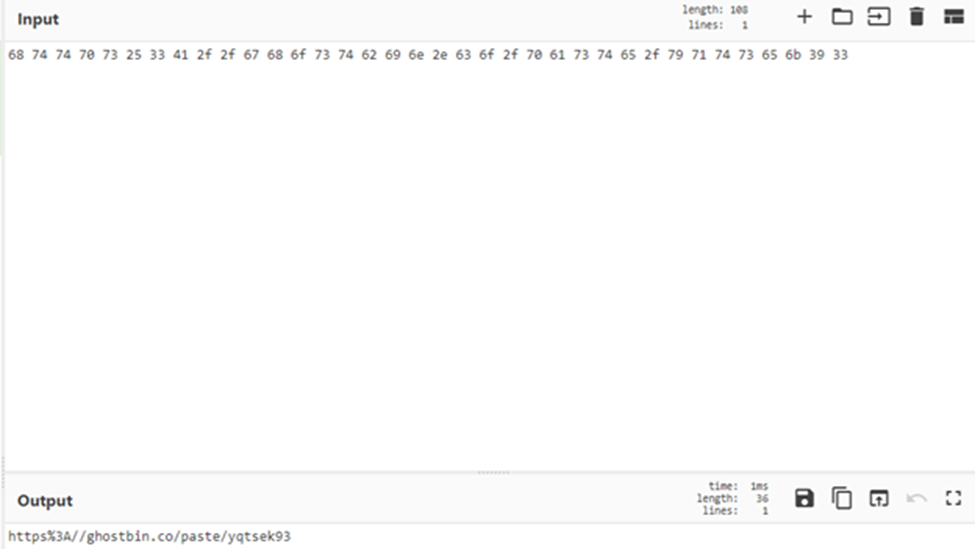
And we get a link.
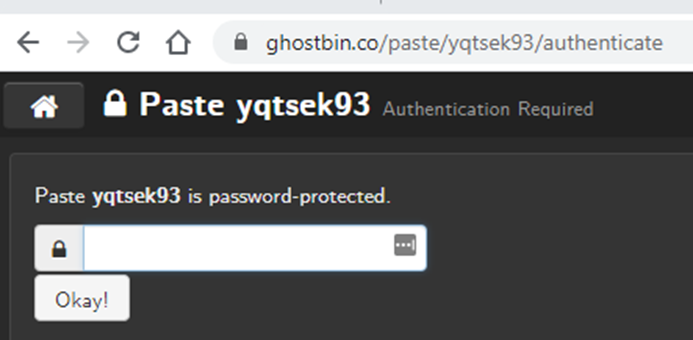
But we need a password.. So lets better search pcap.
On the last http GET request we find a password!
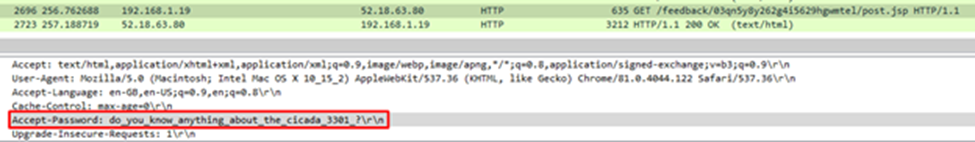
So lets try with this one as the password for ghostbin.
BINGO!!
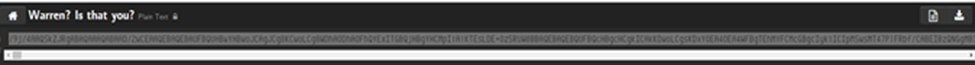
Password was correct and we get a large string that looks like a base64. Lets try to decode from b64!
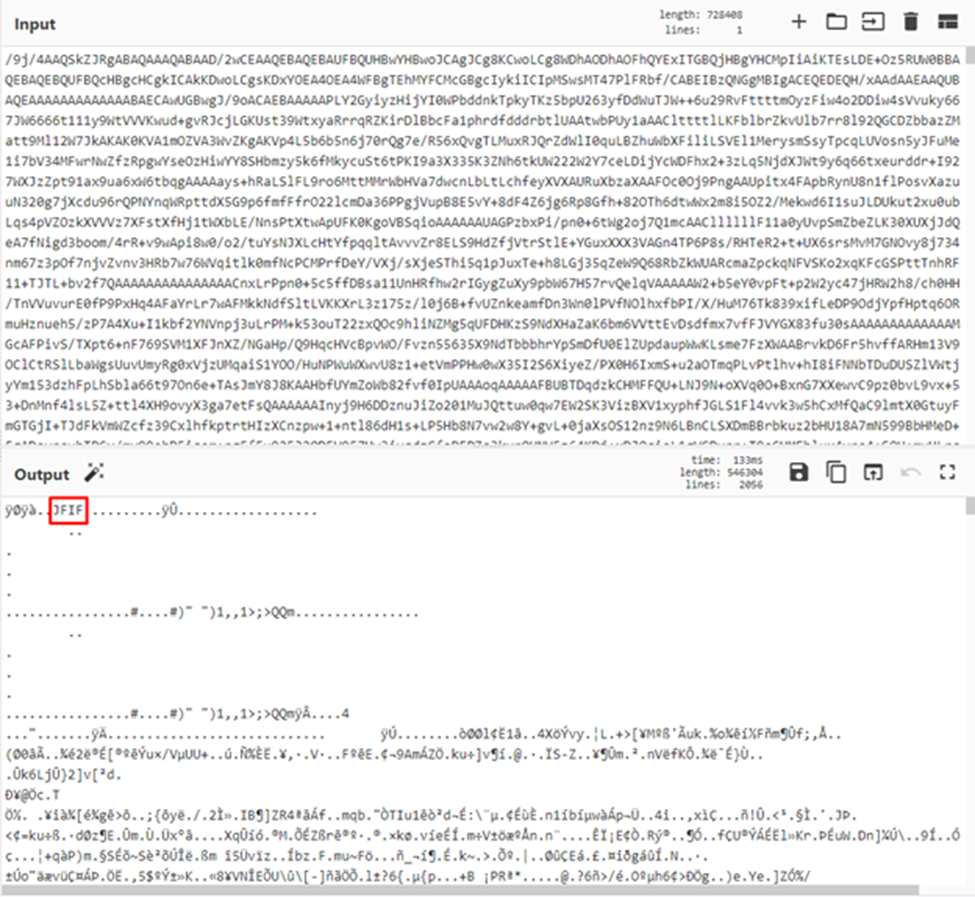

Those are the magic bytes of a jpeg file! Lets convert this base64 into an image.
And we get this image.
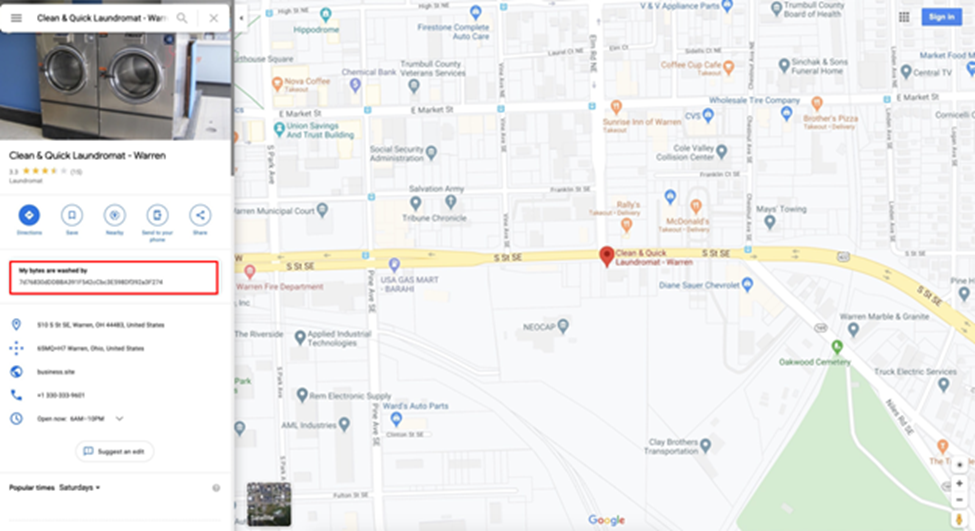
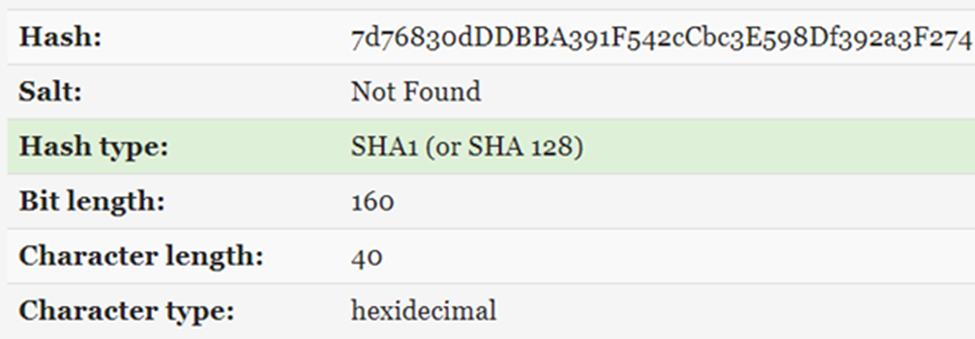
We can clearly see a hash!
It is an Ethereum address of Ropsten Testnet Network!
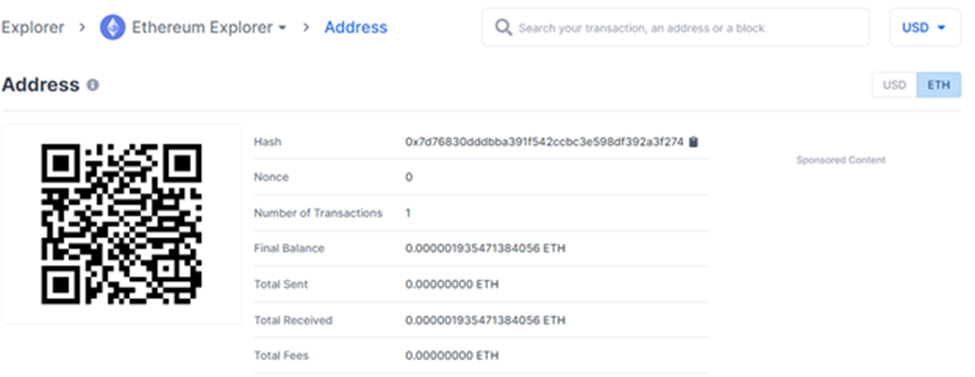
Lets see the last transaction.
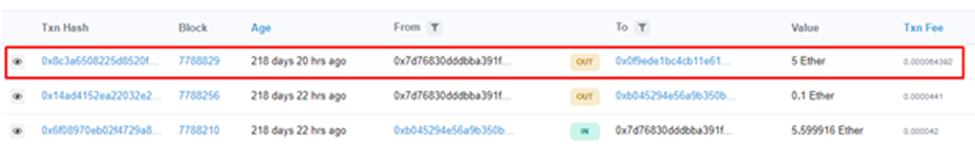
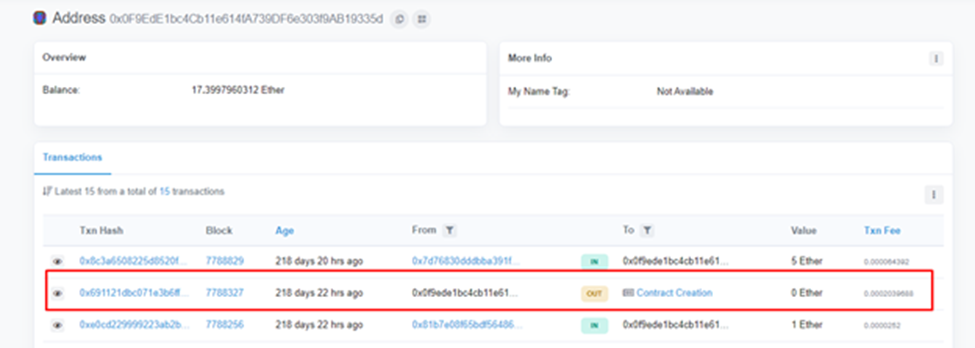
We can get the flag by viewing Input data of Contract Creation Transaction.
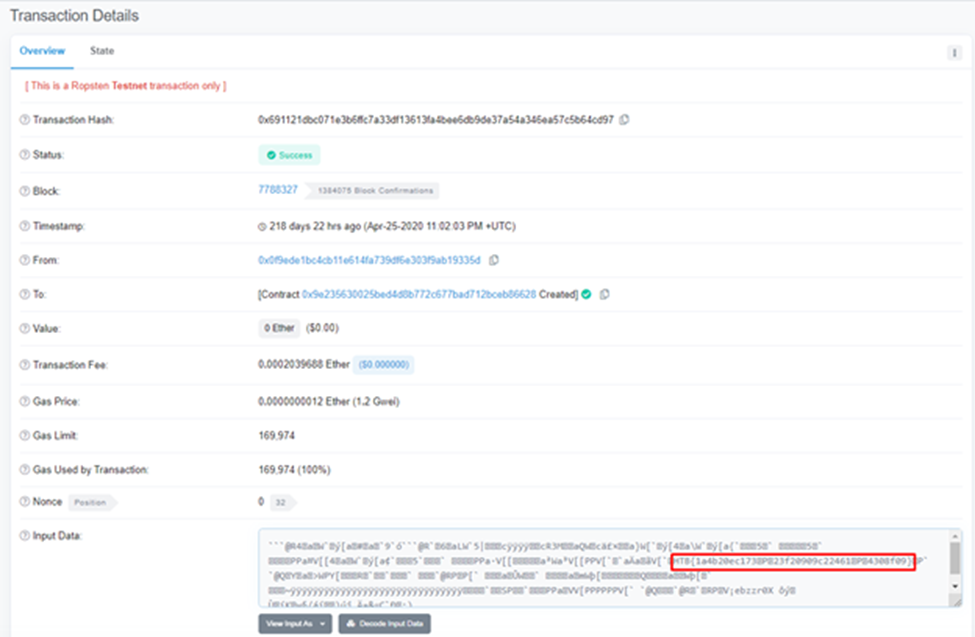
HTB{1a4b20ec17323f20909c224614308f09}
A more elegant way to find the flag would be to decompile the bytecode of the contract.
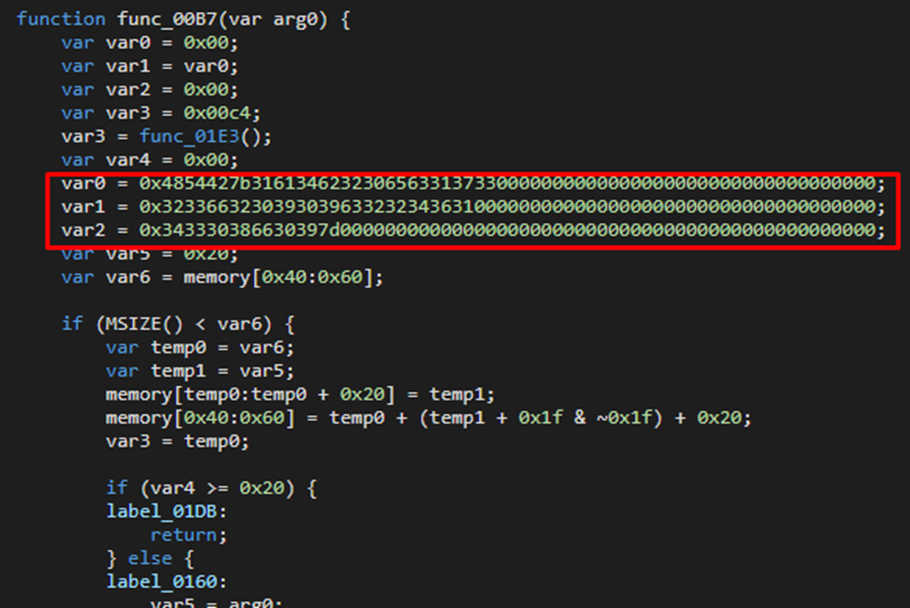
We see those three variables!
Lets convert them to string from hex..
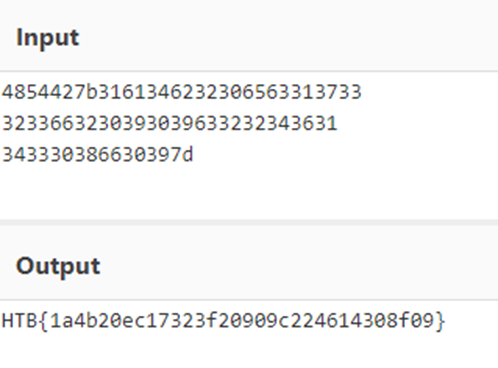
HTB{1a4b20ec17323f20909c224614308f09}
Leave a Reply